Main Risks Of Wireless Networks. How To Protect Them From Hackers

The development and expansion of wireless technologies brought us not only advantages and mobility, but also risks. Wide commercial use of Wi-Fi wireless corporate networks breed the whole new generation of hackers those are oriented on wireless attacks. Here we will analyze the main risks of wireless networking and the ways how to minimize or expel them.
First of all you should know that traditional wired networks use conductor cords to transmit data. They are protected by a couple of serious means. The first line of defense – is a physical perimeter of the building where the network is situated. The other defensive means are Firewalls and IDS/IPS traffic analyzing systems.
So, if a hacker wants to accomplish his goals – he will have to sneak into the building and connect the network directly, or break through the firewall. Wired networks are protected better than wireless due to facts that we will look through later. But even those nets can be easily cracked due to inappropriate use of wireless ones.
You should keep in mind that you will never achieve high security measures with wireless networks, because they are available from rather big distances outside the building. But the fact is that that you will have the possibility to figure out who is hacking from outside the facility by looking at the connection speed. The trick is in that that the weaker the signal is the lower speed of the connection will be, so if you use 100 Mb/s connection and suddenly a 10 or 5 Mb/s connection appears you may be sure that someone is trying to connect you from outside the building.
So, for better understanding of possible ways of protection against wireless threats let’s look through the main of them.
Risk 1 – Outsiders (“rogues”)
Another widespread reason for network hacks is defectively configured hardware that simply has no protection. Frequently those are executive’s tablets or personal notebooks that are not properly configured. They will play as “rogues” giving hackers a chance to hack a network and spread malicious software there.
Risk 2 – Defectively configured hardware
As I have already said – wireless network users are mobile. They connect and disconnect a couple time a day and the moment of connection – is the most dangerous moment in networking. When you connect to a wireless network Wi-Fi devices send packages with the access codes to each other. A hacker can trace and intercept such packages and this way he will know security passwords and your network will be breached.
Risk 3 – Floating connection nature
But not only notebook may be a “rogue”. Such a task can be accomplished by Wi-Fi routers, and many others Wi-Fi compatible devices.
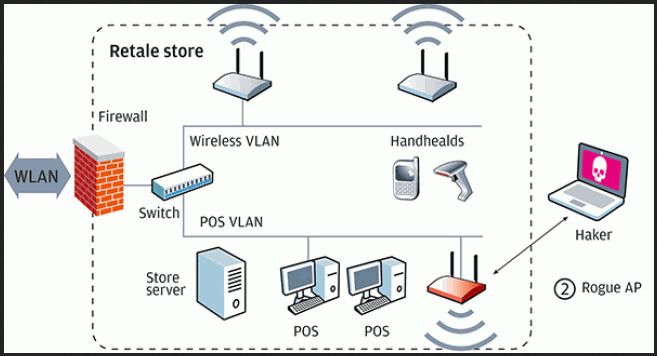
Rogues are the devices that can grant access to a wired corporate network through a wireless one. The classical example is a notebook connected to a local commercial network, with his Wi-Fi adapter active. Sometimes such executives connect to the closest wireless network to surf the net without restrictions or just simply to send some files to his colleagues via Wi-Fi. In that case that device establishes some kind of a virtual bridge between protected wired network and defenseless wireless. So anyone can bypass the security protocols when accessing corporate network through such a device. And that is the most common risk for any network.
Also sometimes an enterprise tries to save some money buying consumer-designed hot-spots and routers, that have weak means of protection. You should always buy enterprise-designed hardware to protect your corporate information.
Risk 4 - Obsolete encryption algorithms
So, you see that wireless technology gives us not only the advantages but also brings a whole new class of risks. Those risks can’t be minimized or expelled by methods used in wired networks. Even a use of Wi-Fi is banned in the organization some executive may connect wireless network and put the entire corporate network to a great risk. That’s more and more companies come to a conclusion that Wi-Fi jamming device may be a suitable solution.
Other protocols such as EAP-FAST or PEAP MS-CHAPv2 are more reliable. Hacker will have to spend more time to hack those. The only “impenetrable” security protocol for wireless networks is WPA2 – Enterprise. But it won’t be so reliable forever.
Many wireless networks still use obsolete security protocols such as WEP or WPA. They can be easily cracked because they broadcast controlling packages in a decrypted form. So the packages that contain the information need for connection can be intercepted by any Wi-Fi station. All that hacker needs is to aggregate some critical mass of packages that are sent through the wireless network and analyze it, so he will have the full access in 5-10 minutes.
But be careful, buying a jammer is not a piece of cake and you will have to really attentive and cautious while choosing a place to buy a jammer and Jammer-Store will be glad to help you with that task!






