XKeyscore Project – NSA's Ultimate Spying And Data Mining Tool

A couple of hours ago we've had a question at our wiki service, regarding the XKeyscore project and we promised to provide a blog post on the topic with the information on the possible means on protecting your personal data from that NSA's ultimate spying tool. So here it goes, but at first, we should try to understand how that system works, to be able to fight it.
Edward Snowden, NSA's whistle-blower provided the information and The Guardian has published it. According t him XKeyscore (XKS) is able to collect and what's most important, process the data of any Internet users, including: browsing and search history, not only from Google, but from other search engines, emails and social networks data.
To view all that data NSA executive doesn't need any kind of warrant or a permission from the higher executives, all he needs is your personal email. So, as Snowden said, NSA executive enters your personal email in the simple online search form, notes the reasons for the search query and the period, data for which is required.
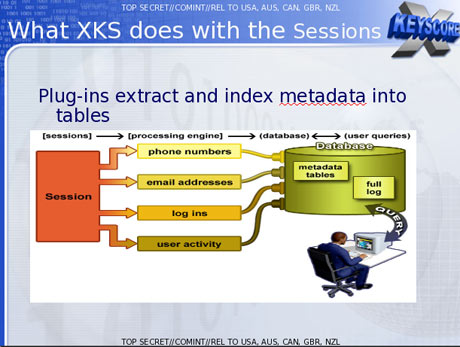
XKeyscore Project
Also XKS allows to identify IP addresses of any user, that visits any host, specified by the executive. The raw data, gathered by that project is really enormous, 1-2 billion of records are added every day. In 2012 there were at least 41 billion of records, stored by XKS for each 30 days period.
Required options
So, as you can see, XKeyscore gives even wider options for spying than PRISM, and it is not controlled in any way. All the data is gathered without your permission and even without your notice, so we've decided to provide you with information on how to protect yourself from such a warrantless spying.
First of all, it is necessary to break any links between you and your actual IP address. To do so just use TOR, and what's more effective VPN. VPN or a virtual private network, will be able to hide an encrypt all your Internet traffic and push it through a couple of virtual hosts. That will make it really hard to detect your actual IP address.

Also, get yourself an anonymous email address, that is not in any linked with your private data, that will probably help. Avoid social networks. You should always remember that social networks are the reason of data leaks, because they not only contain your personal data and log your chat history, they can also process and use as they need.
Using portable jammers
To make sure that your data is safe – avoid using mobile Internet, because mobile Internet connection leads directly to you. Also, modern mobile devices are really vulnerable, especially Android smartphones. Your smartphone will send it's phone number and IMEI to connect the wireless network of your carrier, so be careful with it. As, we've said at our wiki – using of 2G, 3G, 4G portable jammer is recommended to make sure that your data remains yours.
We'd recommend you to keep an eye for your browser's cookies. They may be used to track your activity too, so it will be wise to turn them off in your browser settings, or at least clean them up daily. Remember that the safety of your privacy is in your hands and think well before posting something on the web, especially personal data, because everything posted on the web, remains there.






